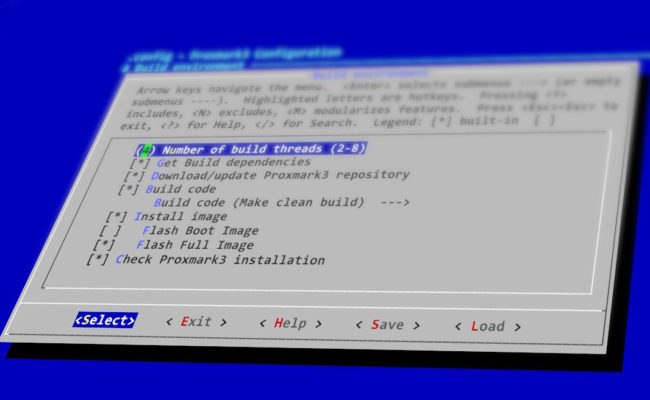
I found myself constantly playing around with the bleeding edge firmware for the Proxmark3, and needed a way to have a consistent build environment no…
Months of development – hours of preparations – seconds to deploy
We often rely on false presemtions that we are secured behind encrypted devices. But how can we be sure?
The best social engineering security strategy is user awareness that these attacks do happen.