Introduction: Why you need to know your data Any organization that wants to be serious about cybersecurity must take a data-driven approach. This means collecting…
The age of hacking has come. But the good news is that you can protect your OT systems by monitoring them to detect any intrusions and anomalies. Check out this blog post for more information.
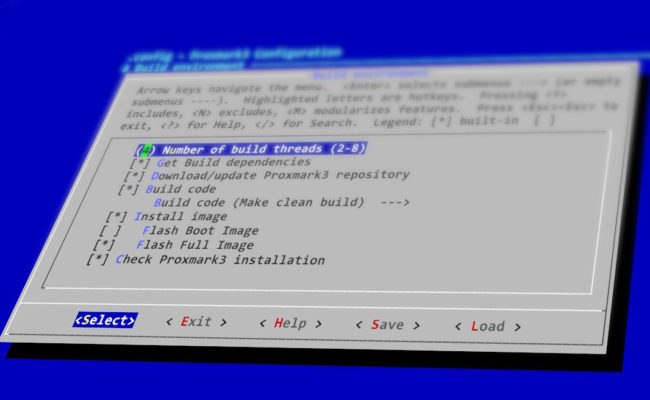
I found myself constantly playing around with the bleeding edge firmware for the Proxmark3, and needed a way to have a consistent build environment no…
Months of development – hours of preparations – seconds to deploy
One day I just got dead tired of that plastic RFID key fob I used to have in my key ring. Every once in a…
We often rely on false presemtions that we are secured behind encrypted devices. But how can we be sure?
The best social engineering security strategy is user awareness that these attacks do happen.







You must be logged in to post a comment.